Google‘s November security update for Pixel phones was issued on time, and judging by the small number of changes visible to users, it seems to be little more than a maintenance update designed to improve power consumption, screen flickering, and the occasional app crash.
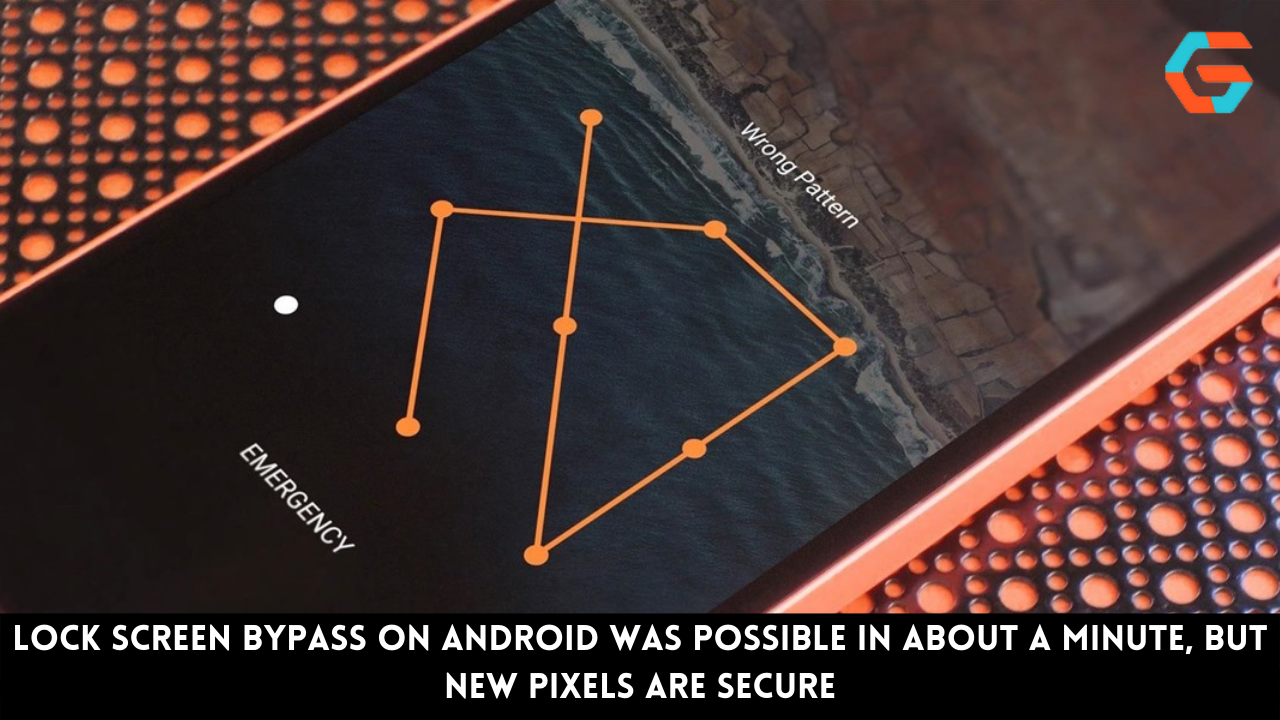
However, this update also patches a critical hole that could have allowed an unauthorized user to unlock a wide variety of Android phones in under a minute using only a physical key or a physical button on the side of the device and no further software or hardware. David Schütz found this way around the lock screen.
Simply replace the original SIM card with the replacement, enter an incorrect SIM PIN code three times, and then enter the PUK code (usually found on the wallet-sized card the SIM came from). Finally, the lock screen will disappear when you follow those instructions. In the video that follows, David shows you how it’s done.
How it Runs
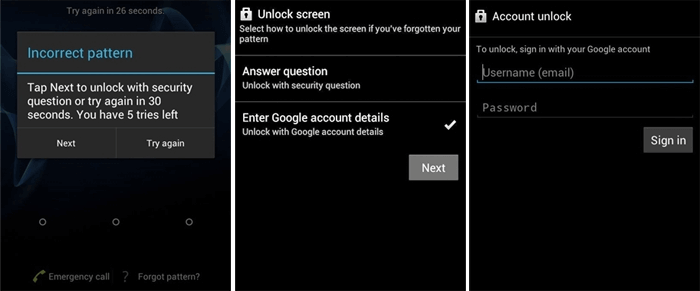
David Schütz‘s blog post provides more context for this flaw; but, to simplify, the issue is related to how Android implements the lock screen, or more precisely, the small group of security screens that includes the normal lock screens and PUK code entering screen. Whenever a security prompt is required, such as during startup or after a power cycle, Android displays it on top and won’t let you ignore it until you meet the requirements (e.g. a valid fingerprint or passcode).
When the conditions are met, the system sends a signal to dismiss the security screen at the top of the stack and return to the next security screen, if any, or to the app or home screen, if none. This flaw originates from an unusual source: a system service that monitors SIM card status changes. In response to a successful PUK code entry and SIM card PIN reset, the SIM card is activated and the PUK security screen is closed by a system service,
which then restores normal lock screen priority. The OS still sent out a notification to dismiss the security screen after it had finished processing the PUK results. Seeing as there was just one security measure left, the standard lock screen, the system mistakenly bypassed it.
What Is Affected?
This bypass does have some limitations, though, as it can only work on a device that has been unlocked since the last time it was booted. The lock screen can be bypassed even if the phone hasn’t been unlocked, but sensitive information and most configuration settings will be unavailable, and the phone will likely have trouble functioning in general until it is rebooted.
Whether or not this method will be effective against devices using the Advanced Protection Program (APP) remains unknown. The flaw, which was first identified on a Pixel phone, is still present in the Android Open Source Project’s code (AOSP).
This means that any devices using software based on this code could potentially be compromised. In addition to GrapheneOS, there have been reports that devices running Lineage are vulnerable to the same exploit. However, there have been rumors that Samsung’s most recent phones are not.
Google Has Published a Bug Fix
The problem is easily fixed by Google. The Android team decided against modifying the SIM activation system service’s functionality, which could introduce new bugs, and instead enhanced the broadcast message to call for a new parameter that indicates the sort of security screen that should be dismissed.
That way, you can clear off your stack of screens without worrying about deleting the wrong one by mistake. CVE-2022-20465 is the official name given to this security hole. In addition to being published by Google in the Android 13 branch on AOSP,
the updates have been backported to the Android 10, 11, and 12 branches as well. Since Google typically alerts its hardware partners to potential security issues before they are made public, it is expected that most manufacturers will soon deploy security upgrades for potentially susceptible devices.
Read More: Reviewing The Microsoft Surface Pro 9: One Step Forward, One Steps Back!
$70,000 Bug Bounty Reward
Through its Bug Bounty Program, Google has awarded many million dollars to security researchers like David for responsibly disclosing bugs like this one. The procedure wasn’t as easy as it should have been, unfortunately. David claims he first tried to report the bug to Google around five months ago, but the search giant rejected his report as a “dupe” and thus ineligible for a reward.

After months of proving the problem to some Google personnel and then following up with a deadline for public disclosure, the issue was finally patched and rectified. This incident highlights the importance of providing ongoing security updates to older phones that are still in use.
Everyone who owns a smartphone could benefit from applying the newest security patches as soon as they become available. Restarting a phone without unlocking it should prevent unauthorized users from accessing your personal information; nevertheless, this is not a practical solution for everyday use.