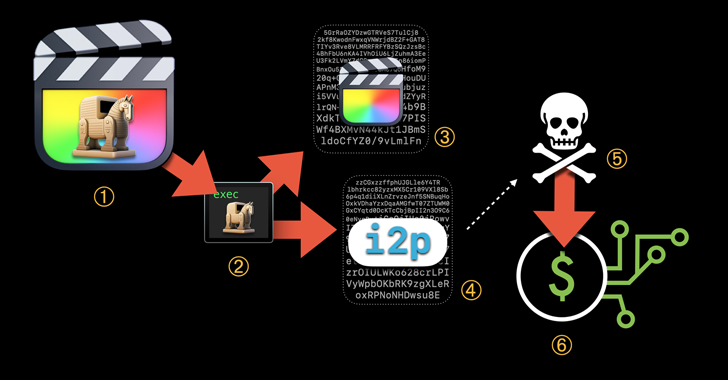
On macOS devices, Trojanized copies of genuine software are being utilised to spread evasive bitcoin mining malware.
The finding was discovered by Jamf Threat Labs, which stated that the XMRig coin miner was executed as Apple’s Final Cut Pro video editing programme, which featured an unapproved alteration.
This malware utilises the Invisible Internet Project (i2p) to download malicious components and deliver mined bitcoin to the attacker’s wallet, Jamf researchers Matt Benyo, Ferdous Saljooka, and Jaron Bradley wrote in a report shared with The Hacker News.
Trend Micro documented an earlier version of the campaign exactly one year ago, noting the malware’s use of i2p to mask network traffic and speculating that it may have been transmitted as a DMG file for Adobe Photoshop CC 2019.
The Apple device management business reported that the source of the cryptojacking apps is Pirate Bay, with the earliest uploads dating back to 2019.
The finding of three generations of the virus, initially spotted in August 2019, April 2021, and October 2021, represents the progression of the sophistication and stealth of the campaign.
An example of an evasion strategy is a shell script that examines the list of running processes for the presence of Activity Monitor and terminates mining programmes if it is detected.
The malicious mining process depends on the user starting the pirated application, at which point the executable’s embedded malware connects to an actor-controlled server through i2p to download the XMRig component.
Due to the malware’s ability to evade detection and the fact that users who install cracked software are knowingly engaging in illicit activity, the distribution vector has been highly effective for many years.
Apple, however, has taken measures to fight such misuse by implementing stricter Gatekeeper checks for notarized apps in macOS Sierra, blocking the activation of modified apps.
Jamf researchers observed that macOS Ventura did not prevent the miner from operating. This malware has already been installed by the time the user receives the error notice.
It prevented the modified version of Final Cut Pro from launching, which could raise suspicions about the user and diminish the likelihood of future launches.
Did you find this article informative? Follow us on Twitter and LinkedIn to have access to additional unique content.
Related Articles:
Apple Is Apparently Closer to Integrating Non-Invasive Glucose Monitoring Technology into Its Watch.
Google, Microsoft and 15 other technology companies headed by Indian-origin executives
There Is a New vintage Technology that Generation Z Is Obsessed With.